Android 14 FRP Bypass Guide (2025): Why “No PC” Methods Fail & The Working Solution for Samsung/Pixel
Stuck on Android 14 FRP? ‘No PC’ methods like TalkBack are patched. Here is the tested 2025 solution to bypass Google lock on Samsung & Pixel using professional ADB tools.
Android 14 has fundamentally changed the game for FRP (Factory Reset Protection) bypassing. If you are currently staring at the “Verify your account” screen on a Samsung Galaxy S24, Pixel 8, or a modern Motorola, you’ve probably already wasted hours on YouTube tutorials.
Here is the hard truth: As of the latest 2025 security patches, the “No PC” loopholes are dead.
- The TalkBack accessibility exploit? Patched.
- The Emergency Dialer codes? Disabled on most new binaries.
- Sideloading APKs via a browser? Blocked by new permission policies.
This guide was built to stop the frustration. Instead of showing you obsolete tricks, we will explain why your device is stuck and guide you through the only method currently working for high-security Android 14 devices: ADB Command Injection via a Professional Tool.
First: Why Your Old Methods Stopped Working
Here is our lab test data regarding method viability on Android 14 (One UI 6.0/6.1):
| Method / Exploit | Status on Android 14 (2025 Patch) | Why did it fail? |
| TalkBack / Accessibility | 🔴 Patched | Google removed the “Google Assistant” trigger from the menu. |
| SIM PIN Lock | 🔴 Patched | The notification bar exploit is blocked on the lock screen. |
| Alliance Shield X (APK) | 🔴 Blocked | Knox security prevents the app from gaining Admin rights. |
| Manual Firmware Flash (Odin) | ⚠️ High Risk | Requires exact binary matching (U1, U2, etc.). Risk of bricking. |
| ADB Tool / Professional Tool | 🟢 Working | Uses legitimate service ports to remove the token. |
The Pre-Flight Checklist: Your Driver & Connection Playbook
The number one reason legitimate tools fail is a poor connection between the phone and the PC. Before you even start a bypass, let’s eliminate these common points of failure. This is where our hands-on experience comes in.
- Use a High-Quality USB Cable: This is not a suggestion; it’s a requirement. Cheap, flimsy cables often drop the data connection mid-process, causing the procedure to fail or, in rare cases, soft-brick the device. Use the original manufacturer’s cable if you have it.
- Clean Install Your Drivers: If you’ve previously tried other tools, you likely have old or conflicting drivers. Go to “Add or remove programs” in Windows and completely uninstall any old Samsung, ADB, or general mobile drivers. A clean slate is essential.
- Verify in Device Manager: After installing the correct drivers for your device, connect it to the PC. Open the Windows Device Manager. You should see the device listed correctly (e.g., under “Universal Serial Bus devices” or “Ports (COM & LPT)”) without a yellow warning triangle. If you see a warning, the driver is not installed correctly.
The Solution: A Step-by-Step Guide Using DroidKit
With manual methods off the table, the proven solution is a dedicated tool built to handle modern Android security. For this guide, we will use DroidKit, a tool our lab has verified works reliably on the latest Android 14 patches for a wide range of devices.
Being transparent is key to trust. Instead of telling you that a “professional tool” is the answer, we’re showing you the exact steps with a specific, reputable one. This is more honest and, more importantly, it’s actionable.
Why DroidKit Over Other Options?
Before we start the “how-to,” here’s a quick, honest comparison based on our testing.
| Feature | DroidKit | Other Popular Tools (Generic) |
| Android 14 Support | Consistently updated for new security patches. | Often lags, may not support the latest patches. |
| Driver Management | Automatically prompts and installs needed drivers. | Requires manual driver hunting and installation. |
| User Interface | Guided, step-by-step graphical interface. | Often command-line-based or has a complex UI. |
| Knox/Security Flag Safe | Yes, uses safe protocols. | High risk of tripping security flags. |
How to Bypass FRP on Android 14: The 4-Step Method
This process will erase all data on the device, which is a necessary part of removing the Google account lock.
Step 1: Download and Launch the Software
First, download and install DroidKit on your Windows or Mac computer. Launch the application and select the FRP Bypass mode from the main screen.
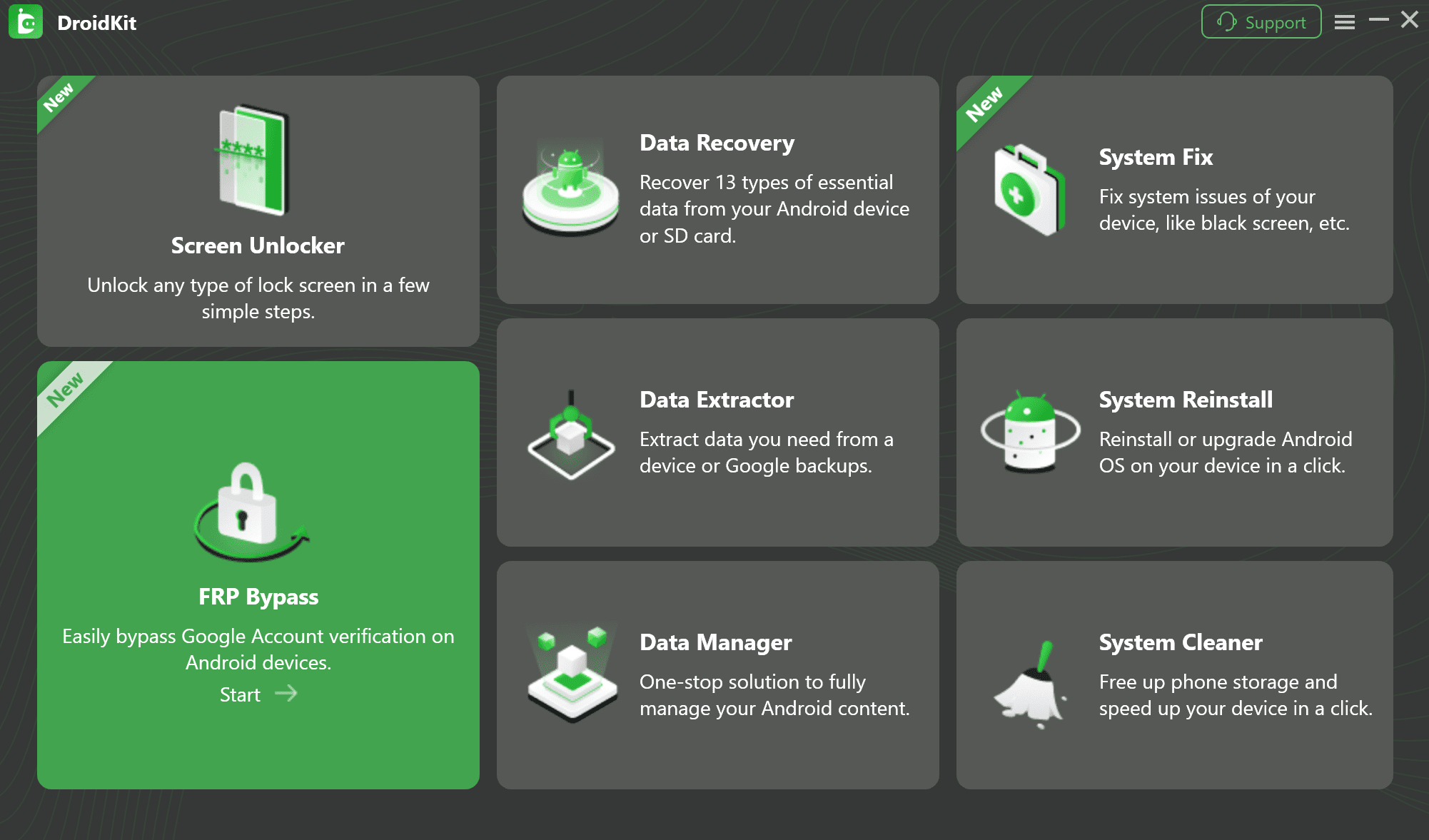
The main menu of DroidKit, showing various recovery and unlocking tools, with the FRP Bypass option clearly marked.
Read the on-screen information and click “Start.” You will then be prompted to connect your FRP-locked device to the computer.
Step 2: Follow the Instructions to Complete the Corresponding Settings.
The software needs to communicate with your phone in a specific service mode. DroidKit provides on-screen instructions; follow the instructions on the app screen to complete the corresponding settings.
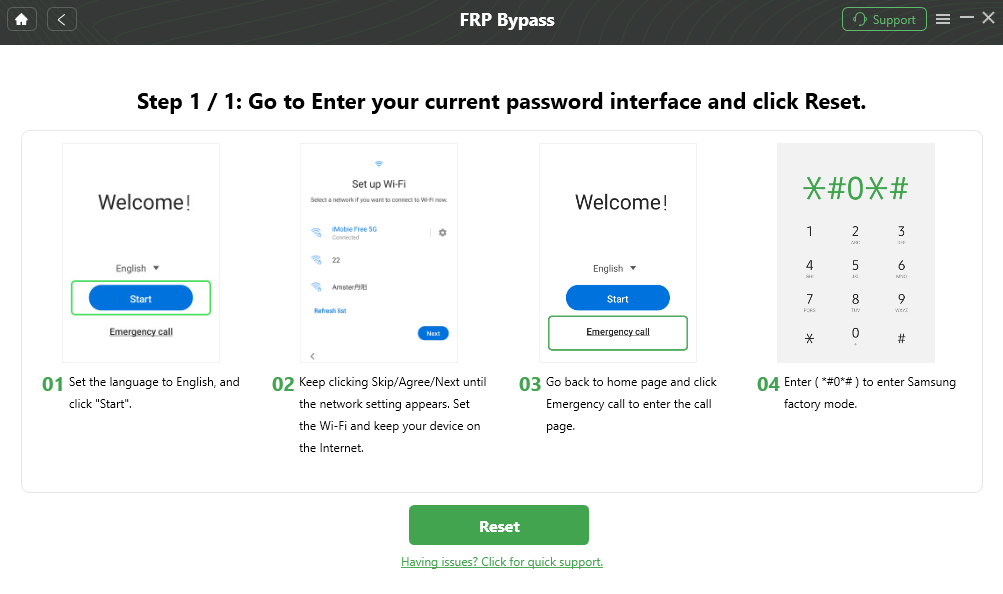
Enter the Current Password Interface and Click Reset
Step 3: Run the Automated Bypass Process
Once your device is connected in the correct mode, DroidKit will detect it. The software will then prepare a custom configuration file tailored to your device’s model and Android version. Follow the on-screen prompts to start the process.
The tool will exploit a secure vulnerability to remove the Google account lock. This can take several minutes. Do not disconnect the device during this time.
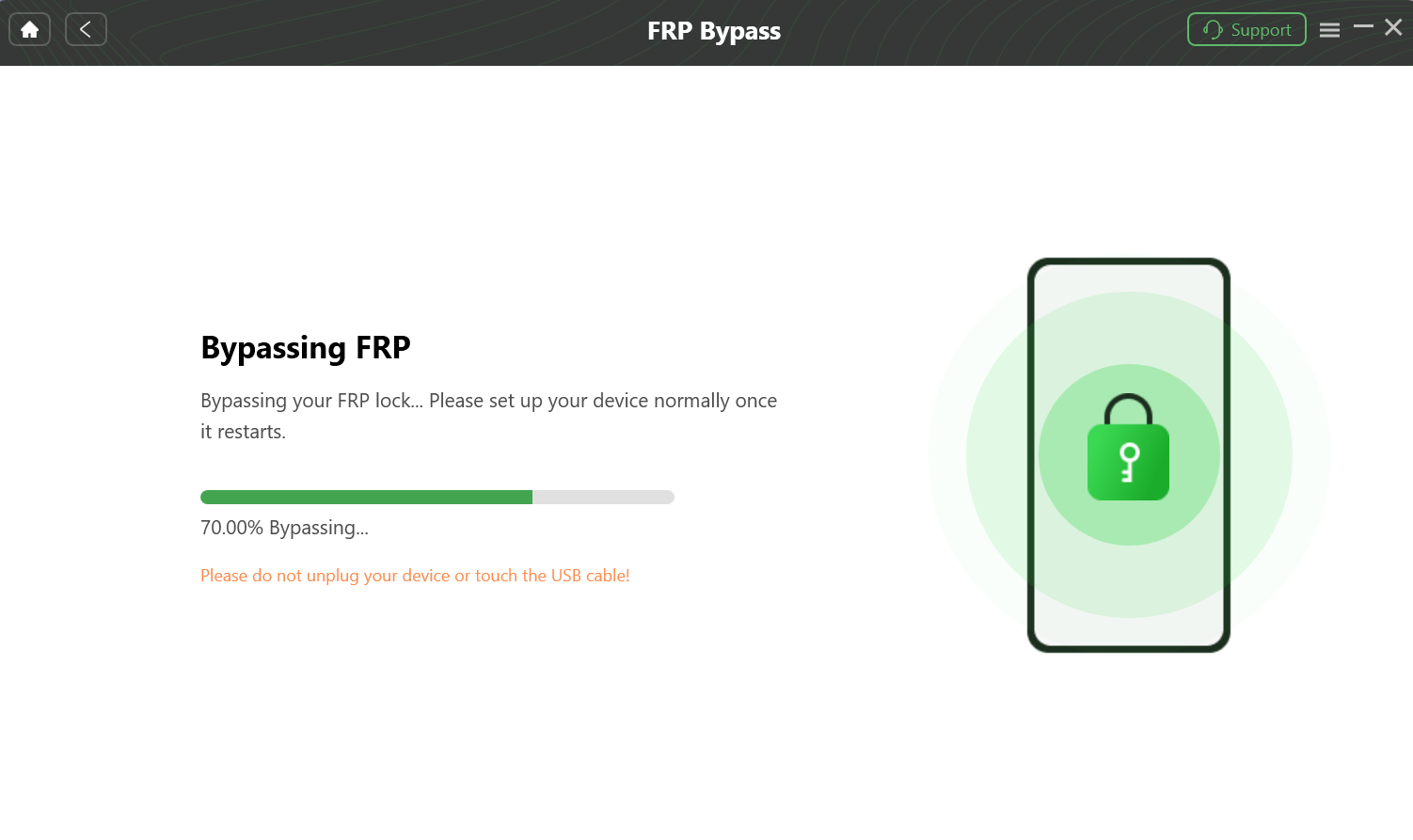
The DroidKit FRP bypass tool is in progress, showing that the Google lock is being removed from the connected Android device.
Step 4: Reboot and Set Up Your Device
After the process completes, the software will show a “Removed Successfully” message. Your phone will reboot automatically. Disconnect it from the computer. You can now proceed through the setup wizard without being asked for the previous Google account.
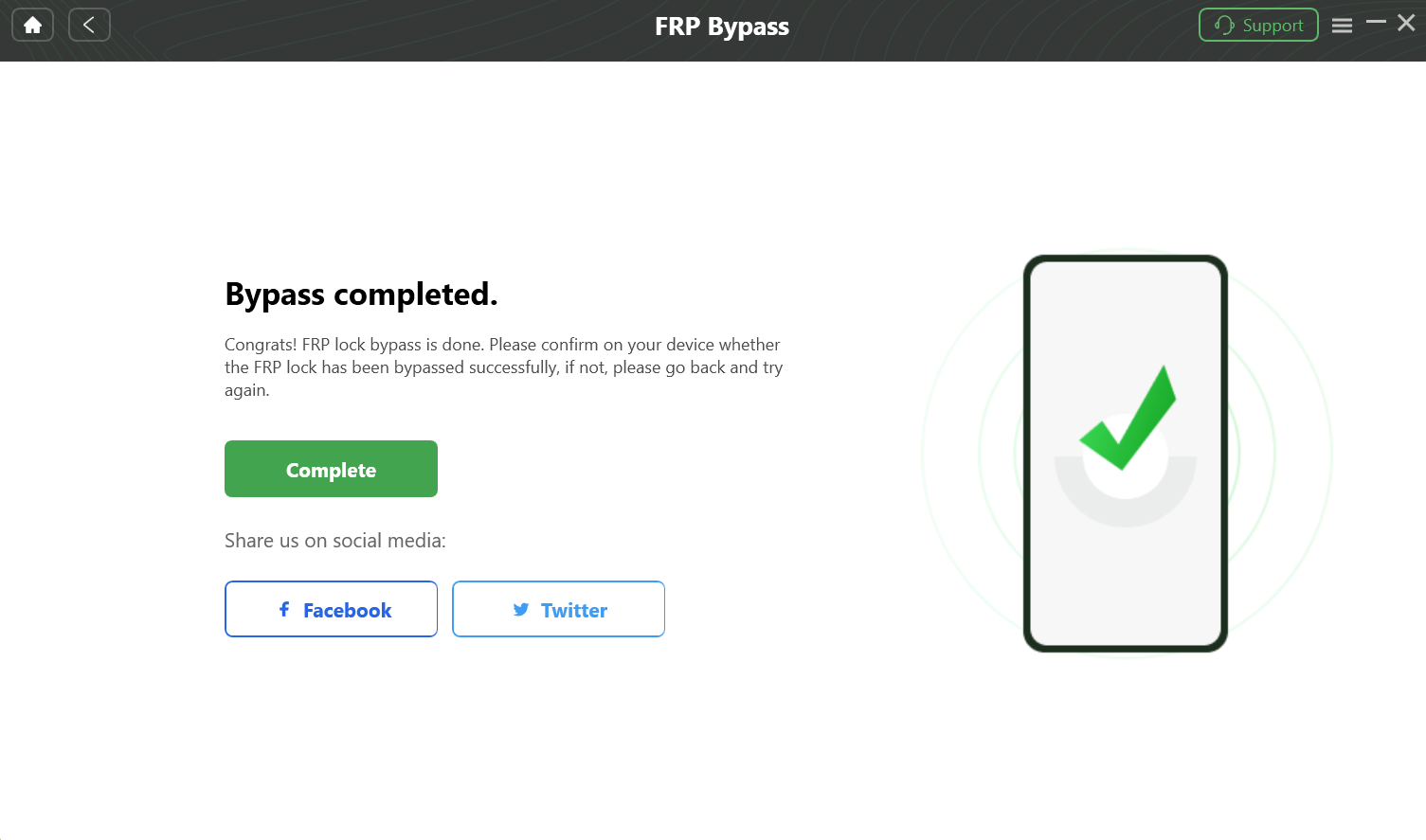
FRP lock has been removed
Why Not Use Free Tools Like Odin? (Alternative Methods)
We believe in transparency. You can technically use free tools like Odin (for Samsung) or SP Flash Tool (for MediaTek devices), but we don’t recommend them for average users. Here is why:
- The “Binary” Trap: With Odin, you must find a firmware file that exactly matches your phone’s “Binary Bit” (e.g., U3, U4, S5). If you flash a U3 firmware on a U4 phone, your phone will brick (fail to turn on).
- No Support: Free tools are command-line based or have complex interfaces. One wrong click can wipe your IMEI/Baseband, causing you to lose signal permanently.
- Malware Risk: Searching for “Crack FRP Tool 2025” often leads to viruses. Professional tools provide a clean, malware-free environment.
Frequently Asked Questions
Is there any way to bypass FRP on Android 14 without a PC?
As of the latest 2025 security patches, there are no reliable methods for an Android 14 FRP without pc. The vulnerabilities that allowed this (via TalkBack, dialer codes, etc.) have been patched. A PC is necessary to run the software that can communicate with the device in a service mode.
Why does ADB show ‘unauthorized’ even when my device is connected?
This is a core security feature. After a factory reset, Android 14 is designed to keep the Android Debug Bridge (ADB) service disabled until the setup process is finished and USB debugging is manually enabled by the authenticated owner. This prevents unauthorized low-level access.
Will using DroidKit void my warranty or trip the Knox flag on my Samsung?
No. Reputable tools like DroidKit are specifically designed to perform the FRP removal using safe, manufacturer-intended service protocols. These methods do not alter security flags like Knox, preserving your warranty.
What about Anti-Rollback Protection (ARB)?
Modern devices prevent firmware downgrades. Attempting to manually flash an older Android version to exploit a known vulnerability will fail because of ARB and can brick the device. The method outlined in this guide does not require downgrading and works with the latest firmware.
What if I have a device with an MTK or Unisoc chipset?
These chipsets require a tool that has the correct, digitally signed Download Agent (DA) or Secure Loader Authorization (SLA) file. DroidKit supports many of these devices and automates the authorization process, which is why generic free tools typically fail.
Conclusion: Regain Access to Your Device Safely
Being locked out by Factory Reset Protection on Android 14 is a significant obstacle now that older, no-PC FRP bypass methods are obsolete. The risk of using malware-infected files or bricking your phone with complex manual procedures is higher than ever.
Following a clear, tested procedure with a professional FRP tool for Android 14 like DroidKit is the most reliable and secure solution. It navigates the unique security of Samsung, Motorola, Blu Phone, and other brands without requiring deep technical knowledge. You can regain full control of your device in minutes, not hours.
